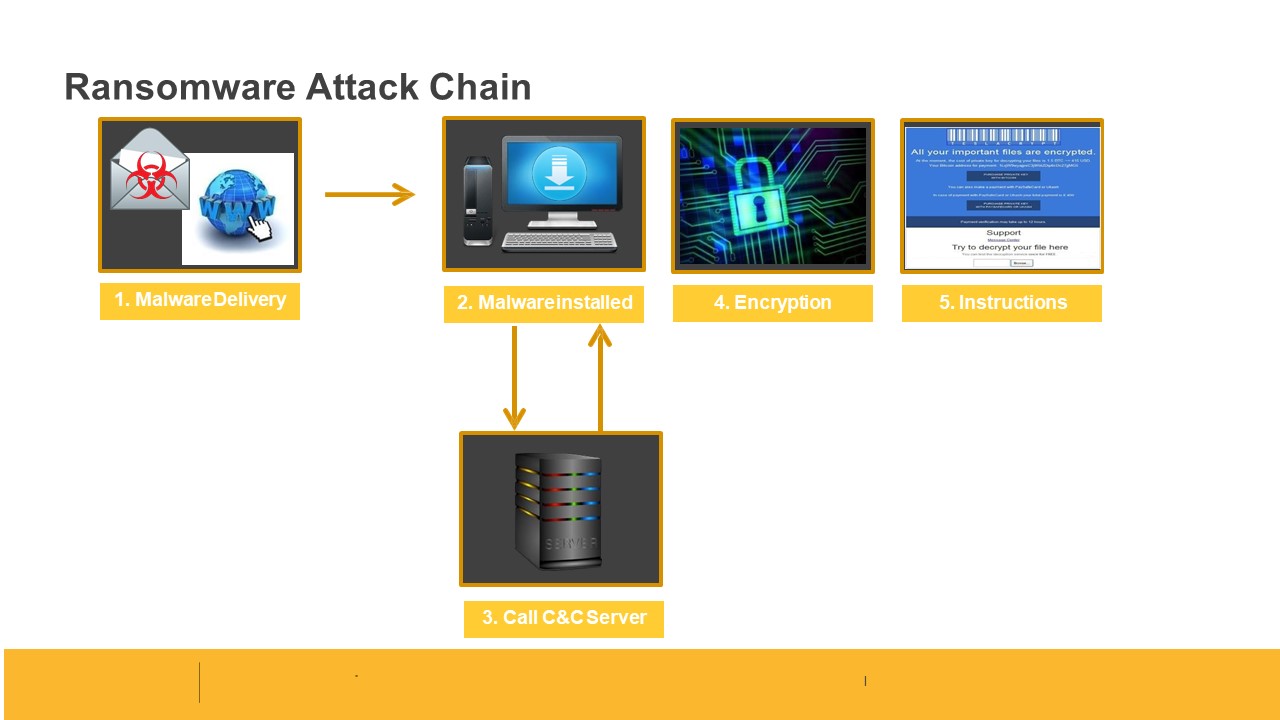
The ransomware is a form of malicious software, it locks and encrypts a victim’s computer or device data, then demands a ransom to restore access.
In many cases, the victim must pay the criminals within a set amount of time or risk losing access forever. And since malware attacks are often deployed by cyberthieves, paying the ransom doesn’t ensure access will be restored.
Ransomware holds your personal data, keeping you from your documents, photos, and financial information. Those files are still on your computer, but the malware has encrypted your device, making the data stored on your computer or mobile device inaccessible.
While the idea behind ransomware may be simple, fighting back when you’re the victim of a malicious ransomware attack can be more complex. And if the attackers don’t give you the decryption key, you may be unable to regain access to your data or device.
Knowing the types of ransomware out there, along with some of the dos and don’ts surrounding these attacks, can go a long way toward helping protect yourself from becoming a victim of ransomware.
Ransomware - State of Play
- Due to its prevalence and destructiveness, ransomware remains the most dangerous cyber crime threat facing consumers and businesses.
- Attackers have perfected the ransomware business model, using strong encryption, anonymous Bitcoin payments, and vast spam campaigns to create dangerous and wide-ranging malware.
- The average ransom amount has shot upwards, jumping 266 percent from US$294 in 2015 to $1,077 in 2016. Attackers clearly think that there’s more to be squeezed from victims.
- Detections of ransomware increased by 36 percent in 2016
Types of ransomware
- Ransomware attacks can be deployed in different forms. Some variants may be more harmful than others, but they all have one thing in common: a ransom. Here are seven common types of ransomware.
- Crypto malware. This form of ransomware can cause a lot of damage because it encrypts things like your files, folders, and hard-drives. One of the most familiar examples is the destructive 2017 WannaCry ransomware attack. It targeted thousands of computer systems around the world that were running Windows OS and spread itself within corporate networks globally. Victims were asked to pay ransom in Bitcoin to retrieve their data.
- Lockers. Locker-ransomware is known for infecting your operating system to completely lock you out of your computer or devices, making it impossible to access any of your files or applications. This type of ransomware is most often Android-based.
- Scareware. Scareware is fake software that acts like an antivirus or a cleaning tool. Scareware often claims to have found issues on your computer, demanding money to resolve the problems. Some types of scareware lock your computer. Others flood your screen with annoying alerts and pop-up messages.
- Doxware. Commonly referred to as leakware or extortionware, doxware threatens to publish your stolen information online if you don’t pay the ransom. As more people store sensitive files and personal photos on their computers, it’s understandable that some people panic and pay the ransom when their files have been hijacked.
- RaaS. Otherwise known as “Ransomware as a service,” RaaS is a type of malware hosted anonymously by a hacker. These cybercriminals handle everything from distributing the ransomware and collecting payments to managing decryptors — software that restores data access — in exchange for their cut of the ransom.
- Mac ransomware. Mac operating systems were infiltrated by their first ransomware in 2016. Known as KeRanger, this malicious software infected Apple user systems through an app called Transmission, which was able to encrypt its victims’ files after being launched.
- Ransomware on mobile devices. Ransomware began infiltrating mobile devices on a larger scale in 2014. What happens? Mobile ransomware often is delivered via a malicious app, which leaves a message on your device that says it has been locked due to illegal activity.
Who are the targets of ransomware attacks?
Ransomware can spread across the Internet without specific targets. But the nature of this file-encrypting malware means that cybercriminals also are able to choose their targets. This targeting ability enables cybercriminals to go after those who can and are more likely to pay larger ransoms.
Target groups of ransomware and how each may be impacted.
- Organizations that are perceived as having smaller security teams. Universities fall into this category because they often have less security along with a high level of file-sharing.
- Organizations that can and will pay quickly. Government agencies, banks, medical facilities, and similar groups constitute this group, because they need immediate access to their files — and may be willing to pay quickly to get them.
- Businesses that hold sensitive data. Law firms and similar organizations may be targeted, because cybercriminals bank on the legal controversies that could ensue if the data being held for ransom is leaked.
- Businesses in the USA, Canada and UK. Cybercriminals go for the bigger payouts, which means targeting corporations. Part of this involves focusing on the United Kingdom, the United States, and Canada due to greater wealth and personal computer use
Tips for preventing Ransomware attacks
- Instal a security software. To help protect your data, install and use a trusted security suite that offers more than just antivirus features.
- Update your security software. New ransomware variants continue to appear, so having up-to-date internet security software will help protect you against cyberattacks.
- Update your operating system and other software. Software updates frequently include patches for newly discovered security vulnerabilities that could be exploited by ransomware attackers.
- Don’t automatically open email attachments. Email is one of the main methods for delivering ransomware. Avoid opening emails and attachments from unfamiliar or untrusted sources. Phishing spam in particular can fool you into clicking on a legitimate-looking link in an email that actually contains malicious code. The malware then prevents you from accessing your data, holds that data hostage, and demands ransom.
- Do be wary of any email attachment that advises you to enable macros to view its content. Once enabled, macro malware can infect multiple files. Unless you are absolutely sure the email is genuine and from a trusted source, delete the email.
- Do back up important data to an external hard drive. Attackers can gain leverage over their victims by encrypting valuable files and making them inaccessible. If the victim has backup copies, the cybercriminal loses some advantage. Backup files allow victims to restore their files once the infection has been cleaned up. Ensure that backups are protected or stored offline so that attackers can’t access them.
- Using cloud services. This can help mitigate a ransomware infection, since many cloud services retain previous versions of files, allowing you to “roll back” to the unencrypted form.
- Don’t pay the ransom. Keep in mind, you may not get your files back even if you pay a ransom. A cybercriminal could ask you to pay again and again, extorting money from you but never releasing your data
Protect Your Privacy and Digital Life
- 15,4M people experienced identity
- 92% people worry about on-line privacy
- An unprotected PC connecting to the internet will be infected within 4 mins.
- Every 2 seconds there is a new Identity Theft victim
NortonLifeLock is a leader in Protection and Performance. NortonLifeLock provides powerful layers of protection for your device, all in a single solution. While you receive protection against viruses and ransomware, you also get protection against phishing and other online threats as you bank, shop and browse online.